While we do not want every incident handled with a rigid checklist, we do want to make sure that we have a consistent methodology when investigating, isolating, and analyzing an incident. For insider incidents, inconsistent handling issues could end up in labor court, and for incident review of APT, one small detail falling through the cracks would be the difference between accurate analysis or going down the never-resolved rabbit hole. Or, for the attacker, persistence or starting all over again. While the approach should be consistent, the handling needs to be individual to that particular incident. That is where information security officers are challenged – to have the technical breadth to deal with anything from an CSRF attack to a piece of malware written and compiled in Lisp, and totally undetectable by any anti-virus programs or malware analysis (zero day).
The balance in handling incidents comes in at the analysis phase where you start out looking for anything, but even parts of this phase involve procedures – ensuring that triage is complete, the required level of system isolation or sandboxing is setup, backup copies are preserved, and other details. Up to that phase, where events are raised, reviewed, and escalated/closed requires a consistent approach, because during the event handling phase inconsistent handling could break down the whole basis for reporting the incident in the first place. Incidents require resources to review, analyze, report, and close, and most of those resources are not expected to handle incidents full-time.
This further drives the argument for introducing automated workflow – orchestration and automation – into security operations processes. If you have the following workflow for DLP, which is typical, you can see the separate human interactions and email or face-to-face confirmations that need to take place.

A larger event would require many contacts and confirmations to track to closure in this scenario, however, the same workflow would filter out the non-incident items at the first step of the process. DLP workflow automation ensures consistent handling of the escalation workflow and tracking of all higher escalations into the incident handling process to complete event handling. If we take a similar, but more simple process than above, and automate the workflow we have the following:
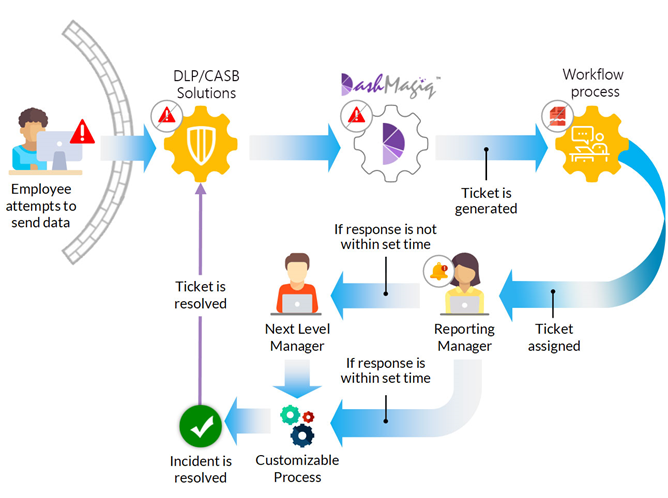
In the above scenario, after the DLP/CASB detects a potentially non-compliant email leaving the network parameter, an alert is issued, the email is quarantined, then a security team member is informed in one step. Without automation, the security team will have to contact the reporting manager and get confirmation, then decide if the response timing is compliant. If not, contact the next level manager and obtain review and approval. Such a process could take a day, or even a couple days. With the DashMagiq orchestration and automation solution, the workflow can be customized for your specific company or industry requirements, then the security reviewer and reporting manager can be sent an alert mail simultaneously; allowing two interested parties to review the event simultaneously and respond much quicker. This would happen in minutes and reduce time spent on such an event by security staff until the events become real issues or escalated to an incident.

